Going phishing? No thanks.
PHISHING. It’s something that, invariably, will happen to all of us.
Phishing is the act of basically taking your details through social engineering – complete a survey to get cash, update your details, log in “for security purposes”, view “important bank messages”, etc. For the people doing the phishing, it’s all about getting your personal details in order to steal your money.
Traditionally, phishing attacks are more “click on a link, complete survey/update details”, but lately they’ve been getting more sophisticated, telling potential targets to “call a number and confirm their details.
From The Age (hat tip to @ashermoses):
But in a new variation on the traditional “phishing” attack, which usually asks victims to click on a malicious link, one Commonwealth Bank scam email asks customers to call a Queensland phone number in order to redeem a $500 “cashback bonus”.
[…]
“It’s an automated system with an American accent that welcomes you to the Commonwealth Bank of Australia and then requests an account number or says something’s expired and asks for your credit card number,” he said.
The voice recording then requested Howard’s expiry date and pin number, but he just entered in random digits.
“It actually told me the information was incorrect, which suggests that it’s hooked up to a payment gateway and it’s actually trying to do an authorisation on the credit card right then and there,” he said.
I’ve been hit three times now – the first time was easy to spot, the second easy as well, and the third time wasn’t so easy (but still contained enough tell-tale signs).

So the first time I was phished I saw it almost immediately – it was an email asking me to read an unread message in my internet banking inbox. There were a couple of things wrong with the actual email, though – not only was it from a YAHOO address (oh c’mon, you gotta try harder than that), there were also tiny errors, such as “Common Wealth Bank” being the name of the sender. It was also sent to the completely wrong email address (the one that isn’t registered to do banking with). The links contained withing the email weren’t particularly useful, either – they both seemed to redirect some bizzaro website, “http://nv-65-40-252-179.sta.embarqhsd.net/” – which doesn’t seem to lead anywhere. Benny 1, Phishers 0.
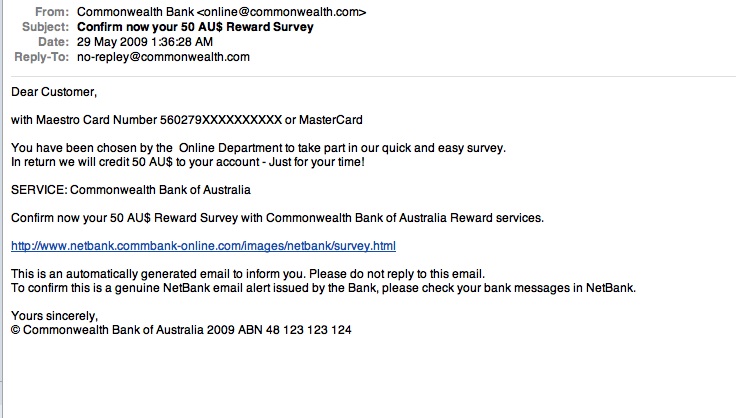
The second time I was phished it was a “complete the survey, earn cash” type. Scarily, some of the details on this email were correct – somehow, they managed to get the first couple of digits on my card right. However, it was the usual elements that gave it away – the email address was “online@commonwealth.com”, with a reply address of “no-repley@commonwealth.com”. Ha. Benny 2, Phishers 0.
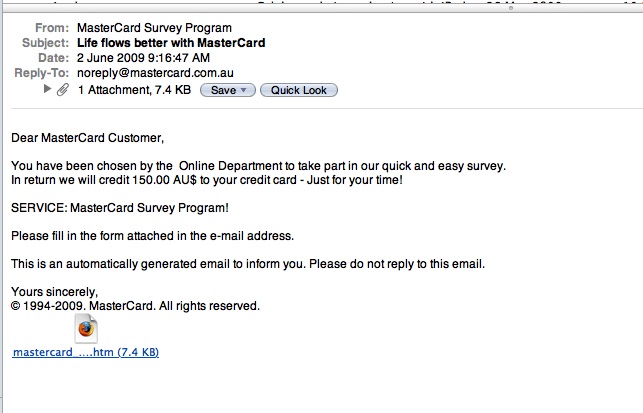
The third time I was phished I was almost caught out. Not only did it seem genuine (all emails addresses seemed legitmate enough), but it was from MasterCard, not the Commonwealth Bank. Sure, it was still a “complete survey, earn cash” type of phishing attempt, but it was a damned good one. There were no links in the email, rather – just a single attachment which contained a single HTML page with an embedded PDF, which contained yet another form. To add to the illusion, legitimate images from MasterCard.com were used, and the email address “info@mastercard.com.au” were also used.
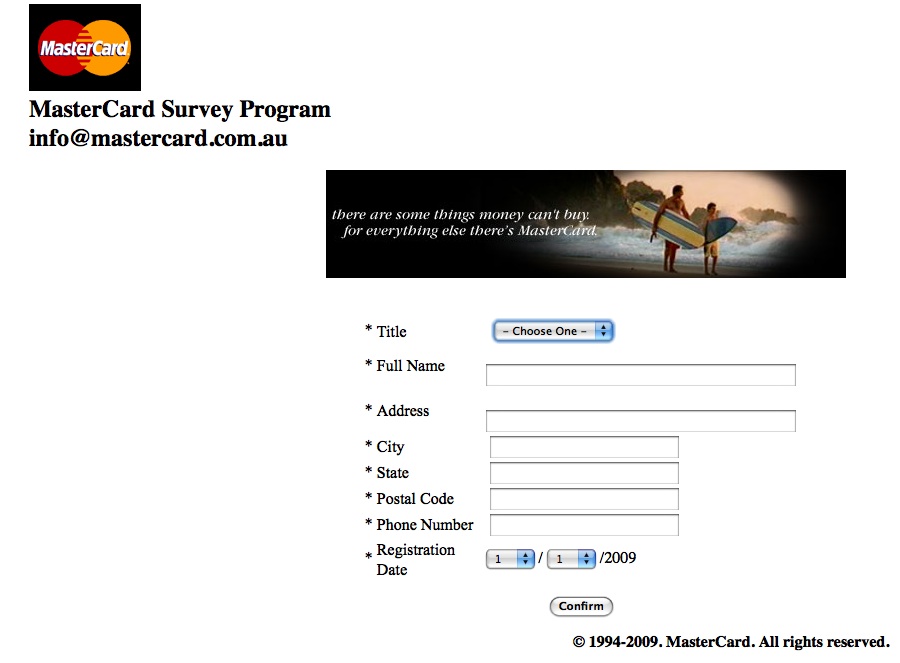
What really started to rung the alarm bells was that the form itself was poorly put together – the boxes didn’t align properly, and so on. The simplicity of the form itself only added to the illusion. Just for kicks, I decided to take a look at the source code of the page itself – and that’s when the alarm bells went off.
Something was wrong with the HTML. Not only did it have no DOCTYPE declaration, but the code was UGLY – lots of horribly put together code. I won’t bore you with the gory details, but it wasn’t how a typical webpage would look.
Long story short – this one was harder to see through, I’ll admit. Only by figuring out the POST of the form (and by that I mean what happens whenever someone clicks “confirm”) did I see that the link it takes you to isn’t a legitimate CBA link, instead, it’s “http://www3.netbank.commbank.com.au.commbanksurvey.com/netbank/bankmain/addcredit.php?checkID=www.commbank.com.au&IdNumber=1280393901″. Er, hello? commbanksurvey.com? That wasn’t the only suspect link, either. “http://www.malala.biz/background2.jpg” was another.
Had I typed in my details and submitted that form, I would have been taken to another legitimate looking site.
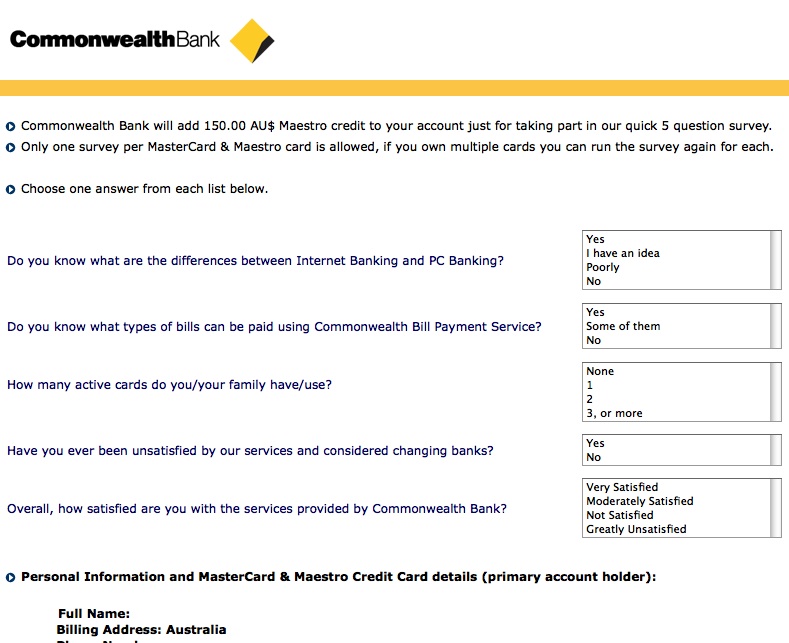
There are a couple of things wrong with this – first of all is no HTTPS. HTTPS is a secure web standard – without boring you with the details, it makes sure that any information you transmit between your computer and the computer you’re communicating with can’t be intercepted and/or easily read by third parties. Go to any online shopping site where you’re asked to enter your credit card details, and you’ll noticed that the URL will begin with https:// – same for any reputable banking institution. However, here was a site without any of that – asking us to input out credit card details. No HTTPS, no survey, no thanks – no matter how much you’re offering.
This last attack is particularly concerning – I would really have no idea how the average internet user would have known to look at the source code, nor how they would have known about the https:// thing. They’d be basically defenseless, seeing as there was no link to click on in the first place, only a web page/PDF.
Well, the final scores are in – Benny 3, Phishers 0.
Couple of things to be learned here.
- Don’t click on links, no matter how legitimate how the email looks. This could include having the right ABN for your bank – something which is easily verifiable by visiting your bank’s homepage.
- If it’s too good to be true, it probably is. Common sense applies to the world of the intertubes as well, you know.
- If you do receive a phishing email, forward it on to hoax@cba.com.au – this will help the good team at the Commonwealth Bank (hat tip to @ozdj) to combat this menace.
Stay safe, and practice safe internets! 😀